Cyber Scotland Week - The Spread and Impact of Ransomware
Date: 27 February 2024

Today we will look at the immediate effect of a ransomware attack, how it happens, how it spreads, and what it does to organizations.
- A user in one of the services receives an email that contains a link to a report.
- The message in the email appears to come from a colleague and contains some information about the report that shows that it has been written by a senior manager and contains some important information that needs to be dealt with urgently to prevent something happening.
- The user clicks the link and is taken to a website that has no apparent relevance to them. It's just a web page, it doesn't contain anything controversial or worrying and the user closes it and puts the email to one side to follow up later and gets on with some urgent work.
- A short while later, the user's screen locks and displays the image below:
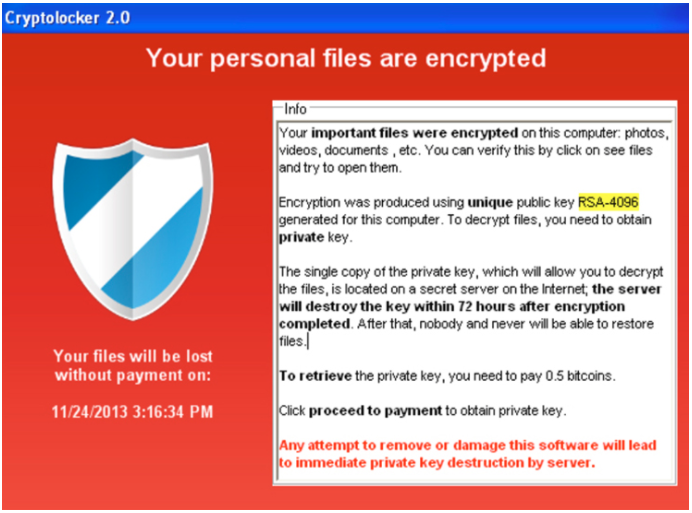
- The computer doesn't respond to any keypresses or mouse actions. The user calls their manager over to see what's happened and the manager contacts IT who tell them to remove the network lead from the wall socket immediately and that someone will be with them shortly to deal with the issue.
- While they are waiting for someone from IT to attend, other members of staff start to report the same issue on their own machines, and some users on currently unaffected machines report that they cannot open any of the files that are stored on their G drive.
- Shortly after, another member of staff reports that their service application server appears to have crashed and that they can no longer log into it.
- IT shut down all network connections in the service area and shut down the service’s G drive and application servers to isolate the problem so that it can be diagnosed safely.
- Other systems across the council network start to fail and become unavailable. Other data storage drives (G drives) become affected, and files become unavailable. It appears that the malware is spreading across the network very quickly.
- The decision is taken that all IT systems should be shut down immediately until the cause and extent of the problem can be determined. At this point nobody knows when or if their systems will be available for use.
From a simple human error (we all make them at some time in our lives), a single click on a link in an unsolicited email (it could just have easily been an attachment that was opened), a cyber-attack has cascaded across the network and has resulted in the complete loss of all IT services.
If you think about the previous day's message and remind yourself of the common signs of a phishing email, you'll quickly see that three of the telltale signs were present in the email.
- Authority: The report was said to be written by a senior manager
- Urgency: The report contained important information that needed to be dealt with urgently
- Emotion: The information the report contained is intended to prevent something happening
The email appeared to come from a colleague and was taken as a credible message, however, a quick check of the source of the email would have prevented the attack from happening.
Thomas Aldred
Service Manager (ICT)
-
Category:
- Events





